Within our company, we run active scans against all systems. On all the Windows servers that is used as on-premise pollers, we run into the following:
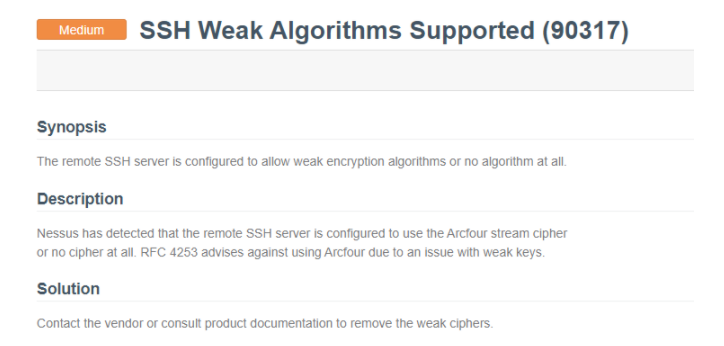
This is showing up on versions 5.1.0, 4.6.3, and 5.0.0. Is there a way to edit the config and/or registry to remove those weak algorithms or on the next update, is there plans to make it more secure? If so, can you provide a date that is planned so I can put in an exception request for all the servers instead of removing it?
Hi csheppard,
Thanks for bringing this up. We are already working to remove the weak algorithms. Please follow this thread for further updates.
Regards,
Krishna.
Dear Sheppard,
We have stopped the problematic service that started in on-premise poller.
In general to remove weak algorithms follow these steps
-
Navigate to the On-Premise Poller installed directory in your system and then open the conf folder.
-
Right-click on the EUMServer.properties file and open it in any text editor. Use the below keys to disable the algorithms in the file. Be careful not to modify any existing keys in the EUMServer.properties file:
-
ftp.exclude.kex.alg
-
ftp.exclude.ciphers
-
ftp.exclude.hamcs
-
ftp.exclude.public.key.alg
-
ftp.exclude.digest
ftp.exclude.hamcs=hmac-sha256, hmac-sha2-256-96
ftp.exclude.kex.alg=diffie-hellman-group-exchange-sha256
# Provide a comma-seperated list of algorithms to be excluded.
#Supported Key Exchange Algorithm : diffie-hellman-group-exchange-sha256, diffie-hellman-group18-sha512, diffie-hellman-group17-sha512, diffie-hellman-group16-sha512, diffie-hellman-group15-sha512, diffie-hellman-group14-sha256, diffie-hellman-group-exchange-sha1, diffie-hellman-group14-sha1, ecdh-sha2-nistp256, ecdh-sha2-nistp384, ecdh-sha2-nistp521, diffie-hellman-group1-sha1ftp.exclude.kex.alg=diffie-hellman-group-exchange-sha256, diffie-hellman-group-exchange-sha1, diffie-hellman-group14-sha256
#Supported Ciphers : ssh1-des, ssh1-3des, aes128-ctr, aes192-ctr, aes256-ctr, 3des-ctr, 3des-cbc, blowfish-cbc, aes128-cbc, aes192-cbc, aes256-cbc, arcfour, arcfour128, arcfour256, [email protected], [email protected]ftp.exclude.ciphers=aes192-ctr, aes256-ctr
#Supported HMAC : hmac-sha256, hmac-sha2-256-96, hmac-sha512, hmac-sha2-512-96, hmac-sha1, hmac-sha1-96, hmac-ripemd160, hmac-md5, hmac-md5-96 ftp.exclude.hamcs=hmac-sha256, hmac-sha2-256-96
#Supported Public Key : ssh-dss, ssh-rsa, x509v3-sign-rsa, x509v3-sign-dss, x509v3-sign-rsa-sha1, x509v3-ssh-rsa, x509v3-ssh-dss, x509v3-ecdsa-sha2-nistp256, x509v3-ecdsa-sha2-nistp384, x509v3-ecdsa-sha2-nistp521, ecdsa-sha2-nistp256, ecdsa-sha2-nistp384, ecdsa-sha2-nistp521, x509v3-rsa2048-sha256, [email protected], [email protected], [email protected], [email protected], [email protected], ssh-ed25519 ftp.exclude.public.key.alg=x509v3-sign-rsa, x509v3-sign-dss
#Supported Digest : MD5, SHA-1, SHA1, SHA-256, SHA-384, SHA-512
ftp.exclude.digest=SHA1, SHA-256
-Jasper
Site24x7, PM
Thank you! I will work on this today and run a remediation scan to make sure it clears.
Sorry for reviving such an old post, but I am wondering if this is still the current method for resolving this vulnerability?
Reason for asking, is because my EUMServer.properties file only contains the following:
Just want to confirm that simply adding the above information is still the correct method to disable ciphers on our Windows on prem poller? Or has it changed to something else in the past couple of years?
Please let me know!
Thanks!
Hi Robb,
Yes, this is the same way to disable SSH algorithms. You may use EUMServer.properties file to mention the algorithms which needs to be disabled in SSH communication as mentioned above.
Regards,
Jenzo
Site24x7